
Modern digital businesses thrive on speed and reliability. Yet, history shows us that no system is immune to failure. A single point of exhaustion—whether CPU, memory, network, or storage—can bring billion-dollar services to a halt. This is where chaos engineering steps in: by deliberately injecting havoc into systems, teams discover weaknesses before real customers do.
In this blog, we’ll explore the four pillars of Chaos Engineering—Starve Application, State Change, Network Assaults, and Application Disruption. Alongside, we’ll revisit real-world outages that underline why preparing for the worst is the smartest strategy.
The Four Pillars of Systematic Failure Testing
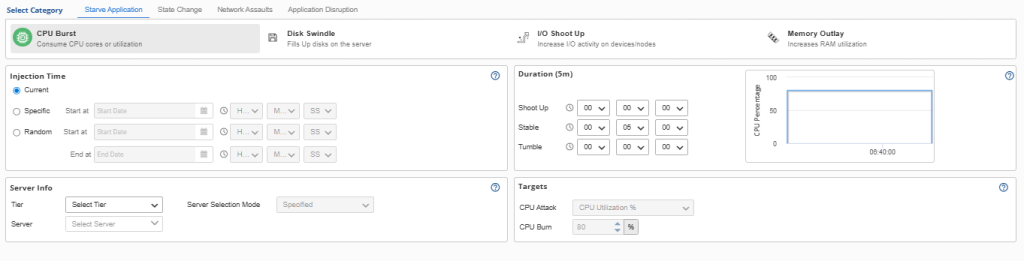
1. Starve Application Attacks
Resource Starvation: When Systems Run Out of Fuel
The first pillar focuses on resource exhaustion—the gradual or sudden depletion of critical system resources that applications depend on to function properly. These attacks simulate scenarios where CPU cycles become scarce, memory buffers fill up, storage space runs out, or network bandwidth becomes constrained.
Key Attack Types:
- CPU Starvation: Consuming processing power until applications slow to a crawl
- Memory Exhaustion: Filling available RAM until systems begin swapping or crashing
- Storage Depletion: Consuming disk space until write operations fail
- I/O Bottlenecks: Creating contention that slows data access to unacceptable levels.
Real-World Example: These scenarios aren’t theoretical. In 2022, Slack experienced significant message delays when memory and CPU starvation affected their infrastructure. Similarly, GitHub’s 2018 outage stemmed from database load surges that created severe I/O contention, demonstrating how resource starvation can cascade through interconnected systems.
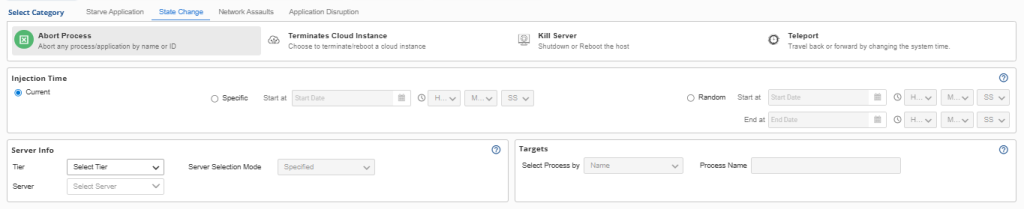
2. State Disruption: When Systems Lose Their Foundation
The second pillar addresses state changes—sudden disruptions to the operational state of processes, services, or infrastructure components. These experiments simulate the abrupt failures that occur when systems lose their foundational elements without warning.
Key Attack Types:
- Process Termination: Simulating application crashes by forcibly killing processes
- Infrastructure Shutdown: Mimicking unexpected VM or container terminations
- Server Failures: Forcing host machines to reboot or shut down entirely
- Time Manipulation: Altering system clocks to break time-dependent operations like authentication tokens or scheduled tasks.
Real-World Example: Google Cloud’s 2020 multi-region outage resulted from a maintenance-related reboot that cascaded across its infrastructure. Twitter’s 2016 service disruption began with server crashes that triggered a chain reaction of failures throughout its platform, illustrating how state changes can amplify across distributed systems.
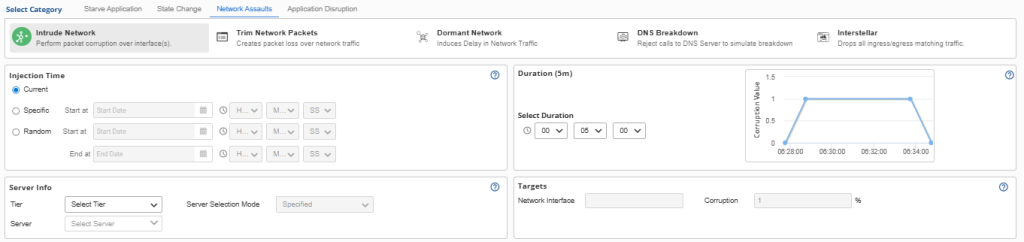
3. Network Assaults
Network Degradation: When Connectivity Becomes the Weakest Link
The third pillar targets network communications—the connective tissue that binds distributed systems together. These experiments simulate the various ways network conditions can degrade, from subtle performance issues to complete communication breakdowns.
Key Attack Types:
- Packet Corruption: Injecting faulty data to simulate hardware failures in network interface cards
- Packet Loss: Dropping network traffic to replicate congestion or hardware issues
- Latency Injection: Adding delays that slow inter-service communication
- DNS Manipulation: Blocking or corrupting domain name resolution
- Network Isolation: Completely severing network connections to simulate major outages.
Real-world examples:
Facebook’s devastating 2021 outage, which lasted six hours and affected billions of users, originated from a DNS misconfiguration that made their services unreachable. AWS’s 2020 US-East-1 incident demonstrated how packet loss in a single region could disrupt businesses worldwide, emphasizing the critical role of network reliability in modern cloud architectures.
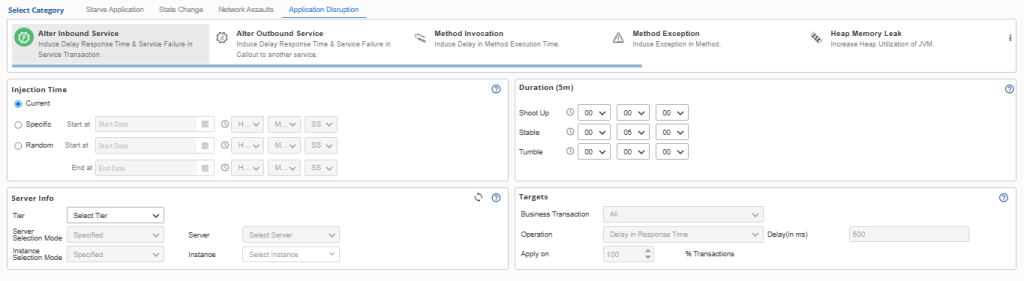
4. Application Disruption
Application-Layer Disruption: When Software Logic Becomes the Problem
The fourth pillar moves beyond infrastructure to focus on application-specific failures. These experiments target the software layer directly, simulating the various ways applications can malfunction even when underlying infrastructure remains healthy.
Key Attack Types:
- API Degradation: Simulating service failures, throttling, or timeout conditions
- Method Delays: Introducing artificial latency in specific code paths
- Exception Injection: Triggering runtime errors to test error handling logic
- Memory Leaks: Gradually consuming heap memory to simulate programming defects.
Real-world examples:
– Microsoft Azure’s 2019 global authentication outage resulted from a memory leak in their authentication services, affecting millions of users worldwide. Netflix, a pioneer in chaos engineering, regularly employs these techniques to validate their resilience strategies, proving that proactive application-layer testing prevents customer-facing incidents.
Why Injecting Havoc is Non-Negotiable
– Downtime costs money: For e-commerce giants, even a few minutes of downtime can cost millions.
– Weak links exist everywhere: From expired certificates to slow DNS, every layer is a potential failure point.
– Preparedness beats firefighting: Simulating chaos empowers teams to handle real incidents confidently.
✅ Key Takeaway: Injecting havoc isn’t about destruction—it’s preparation. It transforms uncertainty into resilience and ensures that when failure strikes, your business keeps running.
Conclusion: From Fragile to Antifragile
Every organization will experience system failures—this is a certainty, not a possibility. The choice lies in how you encounter these failures: reactively, when they surprise you at the worst possible moment, or proactively, when you’re prepared with knowledge, tools, and experience.
Chaos engineering transforms your relationship with failure from adversarial to collaborative. Instead of fearing the unknown, you systematically explore it. Instead of hoping your systems will survive pressure, you know they will because you’ve tested them. Instead of learning about your system’s limitations during customer-impacting incidents, you discover them in controlled environments where learning comes without consequences.
Your competitors are already experiencing chaos in their systems—they just don’t realize it yet. The organizations that will dominate tomorrow’s markets aren’t just building faster features; they’re building systems that get stronger under stress. They’re not just preparing for failure; they’re learning to transform it into competitive advantage.
The future belongs to organizations brave enough to break their own systems before the world breaks them. The question that remains is simple: will you choose to experience chaos on your terms, or will you wait for it to choose you?
Ready to transform your approach to system reliability? Cavisson Systems’ NetHavoc platform empowers organizations to build resilience through intelligent chaos engineering strategies. Discover how NetHavoc can help you turn controlled failure into your competitive advantage—because the strongest systems are those that have learned to thrive in chaos.
Ready to Get Started?
Schedule a demo of NetHavoc today and embark on a journey towards unparalleled reliability and peace of mind. Embrace chaos engineering with NetHavoc and build a resilient future for your applications. Contact us now to learn more!

